Challenge 1:
–[—–>+<]>—-.[—>+<]>—-.+++[->+++<]>++.++++++++.+++++.——–.-[—>+<]>–.+[->+++<]>+.++++++++.–.+++++.——-.–.—-.–[—>+<]>–.++++++.
Answer: brainfuckingeasy
Challenge 2 – “simple” xor crackme with a 55 character password. May make this a higher challenge.
Answer:
“Waxing my car will not result in expert karate training”
challenge 3 – C app, createthread, easy to solve with ida and hex editor or debugger.
Change the timeout for WaitForSingleObject to something higher than 100 ms and you’ll see the messagebox, however the password is on the stack in byte form.
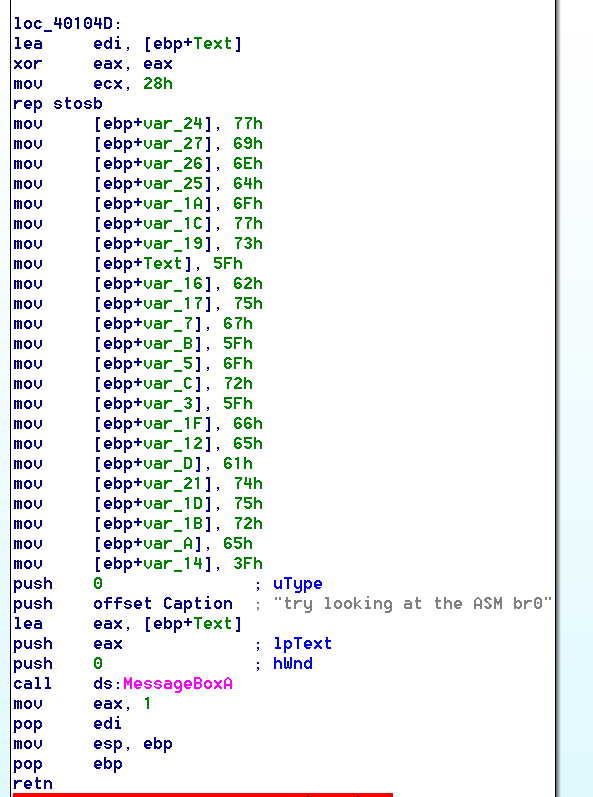
Use a hex editor on each value being pushed to the stack to get the answer: windows_bug_or_feature? I also threw in some anti-debugger code just for kicks.
challenge 4 – java applet with exe inside. Use java decompiler against the jar file, you’ll see “String heytherejoe = “4D5A900003000000040000”, followed by a string to bytes method. Recall that 4D 5A is the hex code for MZ. This is an exe file packed with upx, just run and get answer: c4tus_C0n2016
Challenge 5 – 2 PDF files with exploits inside. Both lead to either a message box or a download + run of http://hda.io/muzac/flag_5.mp3 which is SANIC.mp3, flag is at the end, which is my voice saying “hacksonic” so accept either “hacksonic” or “hack sonic”
Password for the zip is infected
Challenge 6 – python exe file with built in game and flag.
You can use CheatEngine to obtain the score needed, or just decompile with either EasyPythonDecompiler or unfrozen. Optionally you could obtain a pointer to the decompiled code with a debugger, but that’s overkill.
The flag is EasyPythonDecompiler_rocks
Challenge 7 – .net challenge with obfuscator involved. Use de4dot against the binary.
You should see code like this:
static void NothingToSeeHere() { var resourcelist_reference = System.Reflection.Assembly.GetExecutingAssembly().GetManifestResourceNames(); var assembly = Assembly.GetExecutingAssembly(); var resourceName = "CactusCon_Reverse_Challenge_Main.Spraypaintingmyeyes.jpg"; using (Stream stream = assembly.GetManifestResourceStream(resourceName)) { MemoryStream ms = new MemoryStream(); stream.CopyTo(ms); byte[] hashforme = ms.ToArray(); SHA1 shalol = SHA1.Create(); byte[] hio = shalol.ComputeHash(hashforme); string text2 = ""; for (int j = 0; j < hio.Length; j++) { text2 += string.Format("{0:X2}", hio[j] ^ 2); } MessageBox.Show("Good job, the flag is " + text2); } }
The answer is the SHA1 hash of ‘Spraypaintingmyeyes.jpg’, xor’d by 2, or AB875A4DD1AEDC4FB5961981818472D366B06941
The others were just thrown in to confuse the shit out everyone.
Challenge 8 – Macro code that needs to be deobfuscated. Can be done with vbscript, notepad, and text-replace. Here’s the function used to decode:
Private Function DecryptStringFunc(argument) Dim hb1, count, kv1 argument = StrReverse(argument) For count = 1 To Len(argument) hb1 = Mid(argument, count, 1) kv1 = kv1 & Chr(Asc(hb1) - 1) Next DecryptStringFunc = kv1 End Function
Flag is midcitystylespace.com.au
Challenge 9 is an snes rom with some hidden data inside. Zip archive is broken. Included is the rom and emulator.
I broke the pkzip header. It needs to be repaired to work.
See https://users.cs.jmu.edu/buchhofp/forensics/formats/pkzip.html
ie; replace
77 68 61 74 67 6F 65 73 68 65 72 65 3F 3F 3F 00 2B A7 86 48 6B 1B
with
FF FF FF FF FF FF 50 4B 03 04 14 00 00 00 08 00 2B A7 86 48 6B 1B
The cheater’s way is to use 7zip which ignores headers and looks for other structures and you’ll find the flag in jpeg form. The flag is ‘snes_butthead’.
Final challenge is this:
Zip file with password not provided. Crack it and you’ll see (4skJ0e)
Inside is a broken exe file (PE chars replaced with JO) so fix with a hex editor.
Exe uses custom exception handlers, SSE, MMX instructions, fibonacci sequences, and must be patched to get through. The password is in 2 parts, encrypted xor style. This is the flag –
mikudayo-fumifumi
Fastest way to beat this is with a debugger and setting the EIP to 0040116e and single stepping, seeing the 2 strings pushed onto the stack and the 2 xor keys. Easy peasy.
I look forward to making more next year.
Happy cracking!