It’s been a while, so its time to update the blog.
Here’s a quick utility I wrote for finding hard coded addresses of functions within loaded modules.
What possible reason could there be for hard coding addresses? Shell code mostly. Even then, most decent shellcode will not bother hard coding any addresses as it makes the exploit unreliable on other OS’s.
Example:
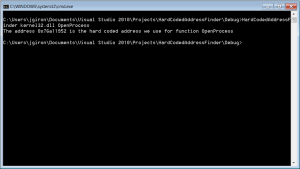
Say I wanted to know the hard coded address of CsrGetProcessId for use within shell code or calling by address within asm. This little program will do this:
#include "stdafx.h" #include <Windows.h> int main(int argc, char* argv[]) { if(argc < 2) { printf("Prints the hard coded addresses of functions for use with shellcode or whatever.\r\n"); printf("Usage is %s dll function-name\r\n",argv[0]); return -1; } FARPROC ptr = GetProcAddress(GetModuleHandleA(argv[1]),argv[2]); printf("The address 0x%8x is the hard coded address we use for function %s\r\n",ptr,argv[2]); return 0; }
So using that,
__asm { mov eax,0x7760cc92 call eax ; ^^ same as call CsrGetProcessId push eax push 0 push 1f0fffh ;PROCESS_ALL_ACCESS / 0C3Ah mov edx,0x76a11952 call edx;OpenProcess test eax, eax jne admin_with_debug_priv ret admin_with_debug_priv: _emit 0xEB _emit 0xFE }
// inliner.cpp : Defines the entry point for the console application. // #include "stdafx.h" #include <windows.h> void BeingDbgd2(); void BeingDbgd1(); int _tmain(int argc, _TCHAR* argv[]) { char *what = "CsrGetProcessId"; FARPROC ptr = GetProcAddress(GetModuleHandle(L"ntdll.dll"),what); printf("%p\r\n", &ptr); printf("The address 0x%8x is the hard coded address we use for %s\r\n",ptr,what); printf("0x%8x\r\n",&ptr); system("pause"); BeingDbgd1(); BeingDbgd2(); return 0; } void BeingDbgd2() { __asm { mov eax,0x7760cc92 call eax ; ^^ same as call CsrGetProcessId push eax push 0 push 0C3Ah;PROCESS_ALL_ACCESS / 1f0fffh call OpenProcess test eax, eax jne admin_with_debug_priv ret admin_with_debug_priv: _emit 0xEB _emit 0xFE } } void BeingDbgd1() { char *fuckit = "fuckthisshitforreal"; int lol = 31; __asm{ xor eax,eax int 0x2d inc eax je dbg ret dbg: _emit 0xEB _emit 0xFE } // awesome dont need to use _emit 0x2d printf("%d",lol); printf("%s",fuckit); }
Other than that, I was working through a variant of ‘torpig’ which made some good use of anti-debugging features I don’t normally encounter such as process memory manipulation, section header adding, and anti-dumping. It doesn’t have to be dumped for me to see what’s going on, so I wasn’t too annoyed: