Howdy all!
On this glorious Saturday night we’re going to go over how to unpack the ‘Local-App-Wizard’ packer.
The way the packer works is by creating a suspended process of itself, hollowing it out / allocating the space with memory mapped files, and writing the contents of the unpacked version of itself to this newly created process with WriteProcessMemory, then calling ResumeThread to run the unpacked binary. Since there are no file operations involved, you can’t just run the app and save the file it copies over. Instead, we have to catch the packed app before it runs, but after it has been unpacked.
I don’t really know where this packer comes from, but one can always tell this packer is in use by the identifying string in the packed binary “Local App-Wizard-Generated Applications”.
Another dead give away comes from a CreateFile call that checks for the existence of a particular file ‘C:\myapp.exe’
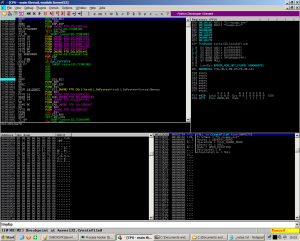
You don’t need much to unpack binaries packed with ‘Local App-Wizard’. I’ll be using Immunity Debugger of course, and my debugger script (python).
First thing we do is load the app, then run my debugger script (type !mybp).
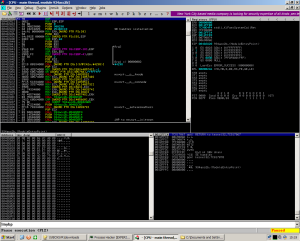
Next, run the app (F9) and skip over any access violations (shift + F9). The first breakpoint we hit will be a createfile call to “myapp.exe” or some variation of it since the writers of the packer keep changing it up.
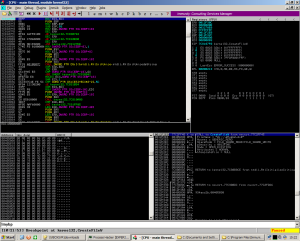
Here is our CreateProcess call with the CREATE_SUSPENDED process creation flag set (0x00000004).
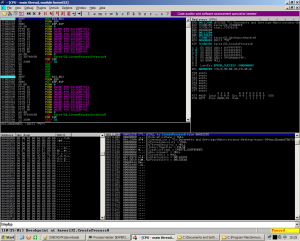
This newly spawned process will hold the contents of the unpacked binary.
Here is our MapViewOfFile call which allows for a file mapping to be copied into the address space of a calling process.
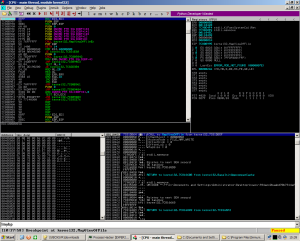
And now, most interestingly is our WriteProcessMemory call. Thanks to bad engineering on the packer writer’s call, all we have to do is follow the address of the buffer pointed to in the API call in our dump to get the unpacked binary.
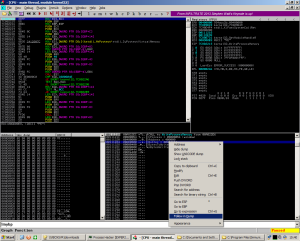
From here, it’s a simple matter of right clicking the dump and saving the output of the dump to a file. Immunity is nice enough to format the file as a binary. The program we saved is complete with section headers, alignment, IAT, and all that other stuff that’s a pain in the ass to restore.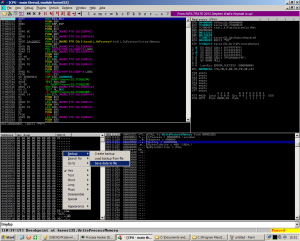
Assuming the newly unpacked program isn’t packed again, we have 2 choices.
1) Wait for the ResumeThread call and dump the RAM for use with Voltality or Process Hacker.
2) Just work with what I have – the unpacked binary.
Lucky for me, the binary isn’t packed twice, so option 2 it is. Browsing in IDA, I have what I want now – C&C info, user agent strings, and the HTTP method which can be used to create a Snort rule.
Maybe one day I’ll write a quick python script to do all of this for me, but for now, it takes like 30 seconds using the Immunity and my script.
You can download the malware lhere. The password is infected.
Happy Cracking!