Hello everyone,
Today we will be going over the answers to the test offered by Tenable / Nessus when you interview with them to be an appsec guy. I was told I was the first to ace all 3 tests, so I might as well be the first to spoil all 3 tests.
What they want is a hash which is provided at the end of the test. It’s 01b689a06ed6be8c01434eb92101d092
Of course you can’t just hand em the hash, you should tell them how you solved the challenges. Here is how:
Question 1)
Solved by a nullbyte after index.php ie: http://restest.tenable.com/?f=index.php%00
look at blank source for this:
<?php /* * Great, you made it! That's already one challenge you knocked out ;) * * Please go to http://restest.tenable.com/497c189133bcdd0f24bd11710e630420.html for the next * one! * */ $file = $_REQUEST["f"]; if ( !isset($file) ) { header("Location: http://restest.tenable.com/?f=main"); exit(0); } $file = $file . ".txt"; if ( strstr($file, "/") ) { $buf = "Invalid character in file name"; } else if ( file_exists($file) ) { $buf = file_get_contents($file); } else $buf = "File not found"; echo $buf; ?>
Question 2)
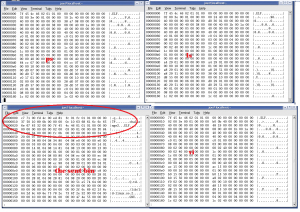
The second one is an archive file, but I wasn’t sure which. Inspecting the header and comparing it (see attachments) showed the header off by about 20 bytes, so a correction with a hex editor made the file right.
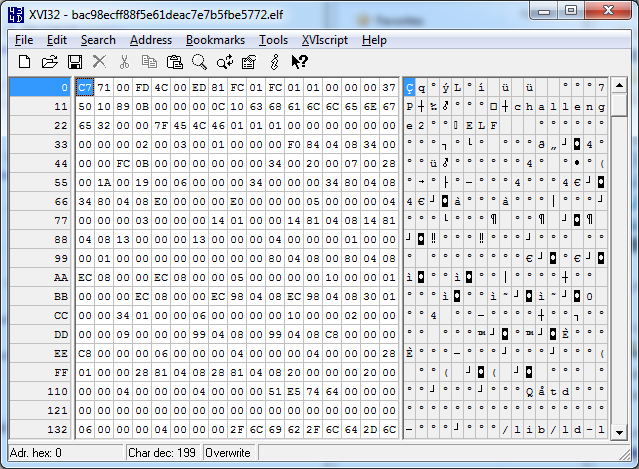
Not quite an ELF file, but you can see the comparison here:
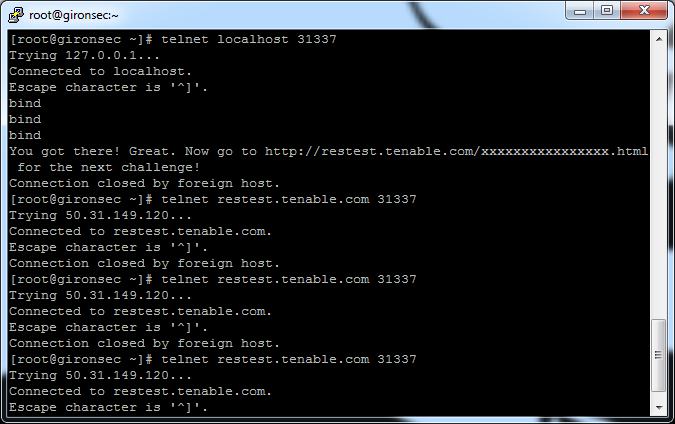
The server is essentially looking for a string by doing a string comparison (typical of the repe cmpsb / setnbe instrctions). It loops for the characters ‘bind’ referenced inside read-only data at 0x08048877
.text:08048707 mov dword ptr [ebp-454h], offset 08048877 .text:08048711 mov dword ptr [ebp-458h], 4 .text:0804871B cld .text:0804871C mov esi, [ebp-450h] .text:08048722 mov edi, [ebp-454h] .text:08048728 mov ecx, [ebp-458h] .text:0804872E repe cmpsb .text:08048730 setnbe dl .text:08048733 setb al .text:08048736 mov ecx, edx .text:08048738 sub cl, al .text:0804873A mov eax, ecx .text:0804873C movsx eax, al .text:0804873F test eax, eax .text:08048741 jnz short loc_8048766
By entering “bind” after telnet-ing to the the service / port, I got the answer for the next part as shown in the next attachment.
Question 3)
Right after the recv call (function that accepts our data) there is a byte comparison checking the length of our input. if its greater than 7, then continue, otherwise the program quits:
.text:08048718 call _recv .text:0804871D mov [ebp-8], eax .text:08048720 mov eax, [ebp-8] .text:08048723 cmp eax, 7 .text:08048726 ja short loc_8048734 .text:08048728 mov dword ptr [esp], 0 .text:0804872F call _exit
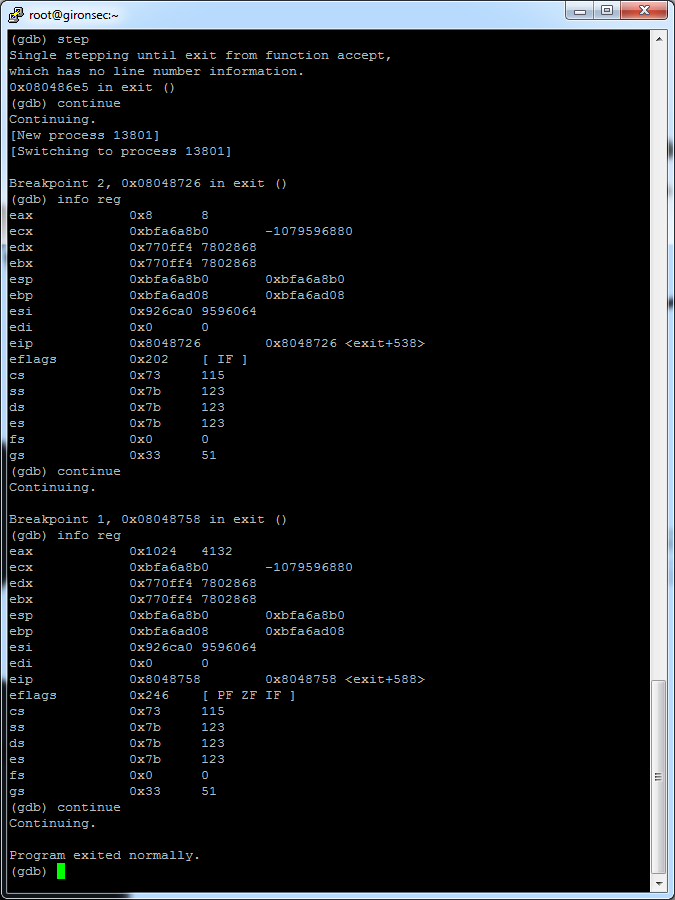
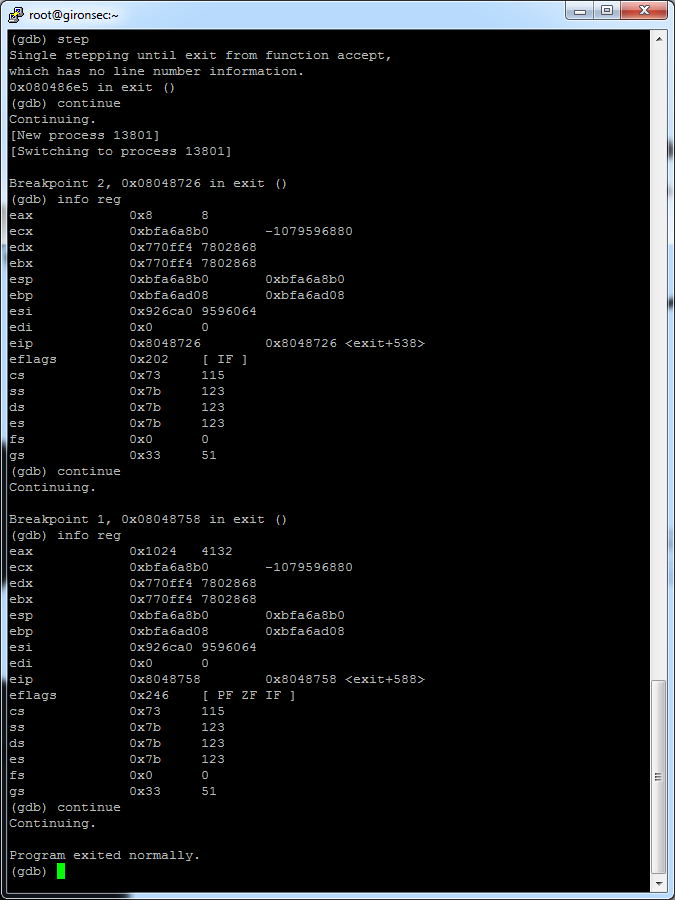
So after passing that I noticed the value sent from the recv() call was being stored into the EAX register, and then doing a numerical / binary comparison against the value stored inside, specifically checking if the value of EAX is equal to 1024 in hex (4132 in decimal):
.text:08048734 mov eax, [ebp-40h] .text:08048737 mov [esp], eax .text:0804873A call _ntohl .text:0804873F mov [ebp-40h], eax .text:08048742 mov eax, [ebp-3Ch] .text:08048745 mov [esp], eax .text:08048748 call _ntohl .text:0804874D mov [ebp-3Ch], eax .text:08048750 mov eax, [ebp-3Ch] .text:08048753 cmp eax, 1024h .text:08048758 jnz short loc_804877F
So all I had to do was stick the value 1024 in hex into the recv call. The problem is it wants something 8 bytes in length, but 1024 is only 2 bytes. I solved this by passing the data with NULL values 0x00 in hex.
I used php to do this:
<?php $host = "restest.tenable.com"; $port = 31338; $timeout = 20; $data = "\x00\x00\x00\x00\x00\x00\x10\x24"; $fp = fsockopen($host,$port,$errno,$errstr,$timeout); if (!$fp) { die("$errstr ($errno)\n"); } else { fwrite($fp,$data); while(!feof($fp)) { echo fgets($fp, 512); } fclose($fp); } ?>
Just copy this verbatim and you too can have a crack at Tenable / Nessus, well at least until they find this and change the answers. Be warned though, they don’t want smart people, they want clay to mold.
Good luck and happy hacking =)
And no, I didn’t forget the funny image.