The triumphant release of Battlefield 3 marks the second time in my life where I waited til midnight to purchase a game standing outside a store. The first of which being Fallout 3 (after all I did wait 10 years for a sequel). And with the newest game out you would think there would be some sort of update right? ….RIGHT?
Nope. Well sorta, but not much. About the only noticeable difference I see is that they modified the UI slightly, but other than that no real code changes are present in the binary.
Now is as good a time as any to reveal some of my findings. For starters we have some call to a telemetry server. It was on port 9922. I noticed this while Iwas monitoring new threads with processmon. After doing a slow as hell text binary search through the code for any references to the IP (159.153.235.32) which was NOT in the strings table (why?) this is what I found:
loc_4020A6:
lea edx, [ebp+var_26C4]
push edx ; int
push offset aTelemetryserve ; “TelemetryServer”
push offset aTelemetry ; “Telemetry”
lea ecx, [ebp+var_249C]
call sub_6D3230
cmp eax, 0FFFFFFFFh
jz short loc_4020D5
mov esi, [ebp+var_26C0]
cmp [ebp+var_26C4], esi
jnz short loc_4020EB
loc_4020D5: ; “159.153.235.32”
push offset a159_153_235_32
lea ecx, [ebp+var_26C4]
call sub_408CE0
mov esi, [ebp+var_26C0]
A telemetry server!
EA owns the IP range so I assume this is part of their tracking system
http://whois.arin.net/rest/net/NET-159-153-0-0-1/pft
What does it send? XML of course! But what contents? This is what I have been able to extrapolate:
Initial connection is made, it sends the following markup:
<TELEMETRY_XML>
<!– new session: BEGIN –>
<internal persona=”%s” UUID=”%I64x” nucleusId=”%s” locale=”%s” />
<Metric Module=”%s(internal ID %u)” Group=”%s(internal ID %u)” String=”%s tm_API=”%i”
timeStamp=”%I64x (%.4i-%.2i-%.2i %.2i:%.2i:%.2i)” />
<!– new session: END –>
Then it sends a bunch of binary data. This is likely the encoded information about your system. I have yet to decode it.
Since this is a C based library its using format string identifiers. You see strings, integers and their widths. The persona field is your sign on name. The nucleus ID is the same thing.
The locale is the region (in my case USA), the metric module is something (???) same with the internal and group ID’s. Not sure what they are for yet. The tm_API is just some number. Lastly we have the 64 bit time stamp. Easy enough to follow and easy enough to filter through with wireshark.
There is other stuff that I see from time to time that connects or listens, but its mostly dumb stuff like news feeds and an amazon service.
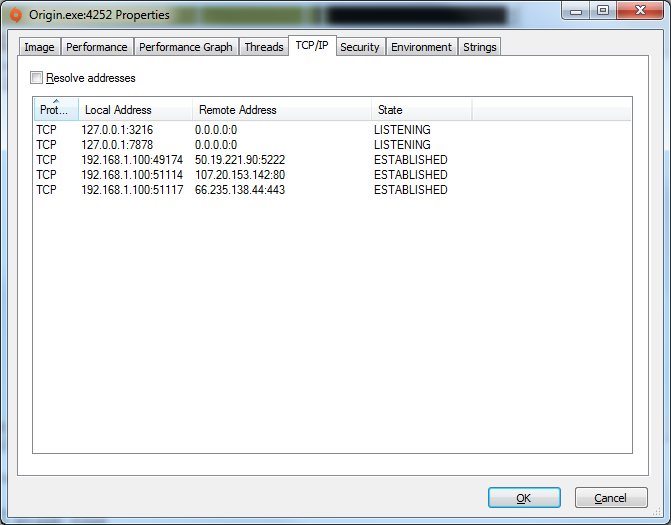
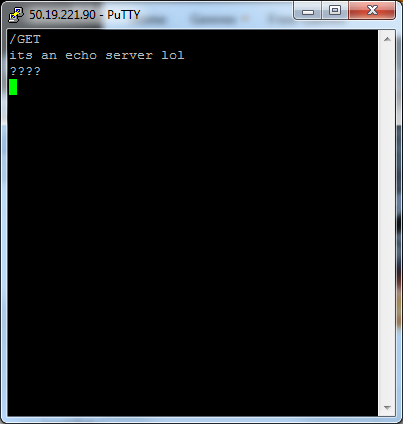
The 50.19 address belongs to amazon according to ARIN:
http://whois.arin.net/rest/net/NET-50-16-0-0-1/pft
Connecting to it with a raw socket yields nothing in terms of a banner or header. Its a damn echo server.
You can look up the other ip’s you want, but I already saw most of them – web site connections made by the clients.
There is a lot more stuff to document so I will continue this with part 3 when we go over the browser plugin.