From time to time, I encounter….weird forms of software protection. Stuff most other reverse engineers have probably never seen.
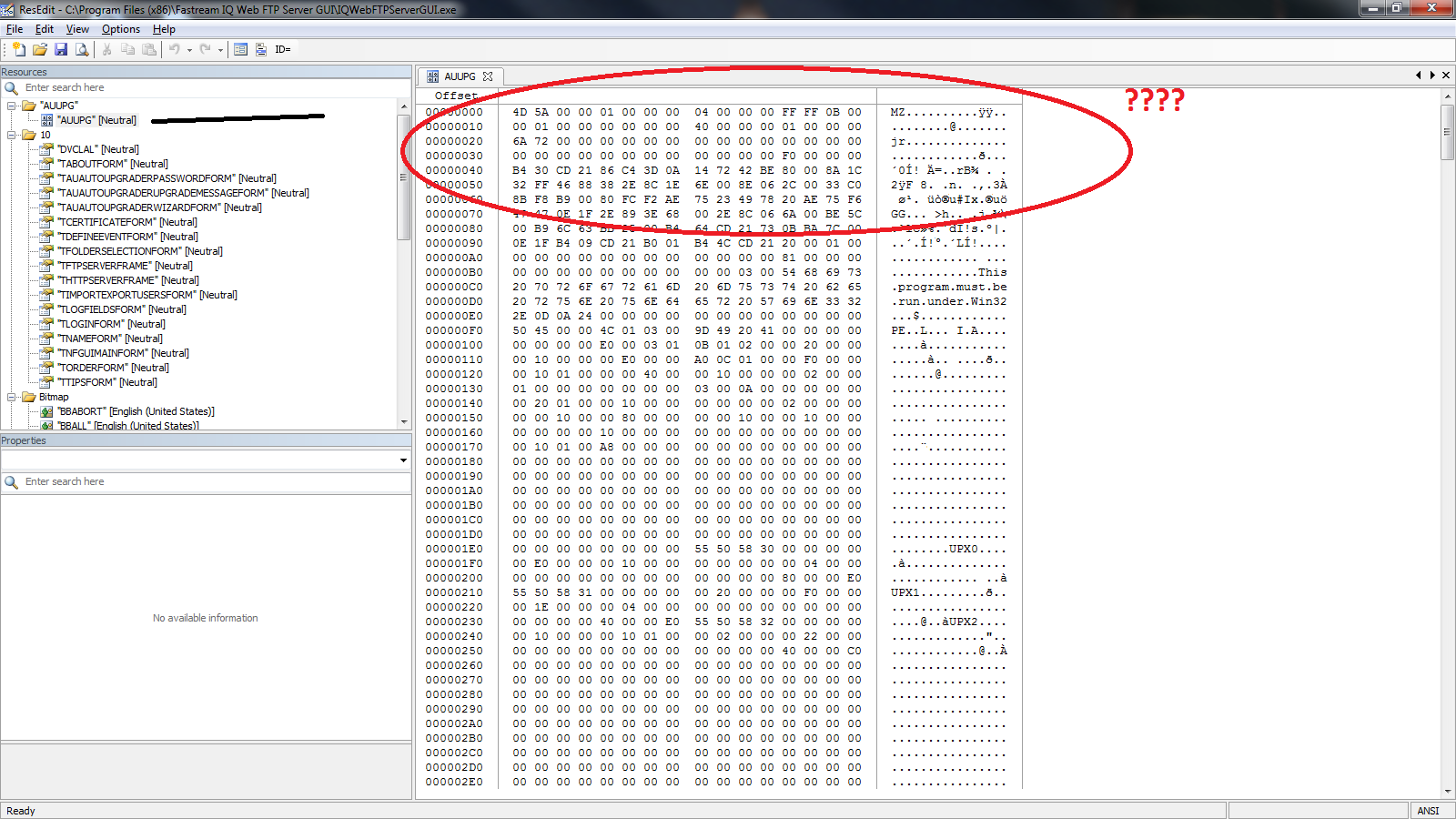
Take this example. I was trying to track down a string in a binary, but couldn’t find it through conventional means, so I opened the program up with a resource editor. Then i stumble upon this weird section. See it? Some resource table named “AUUPG” with a bunch of jibberish.
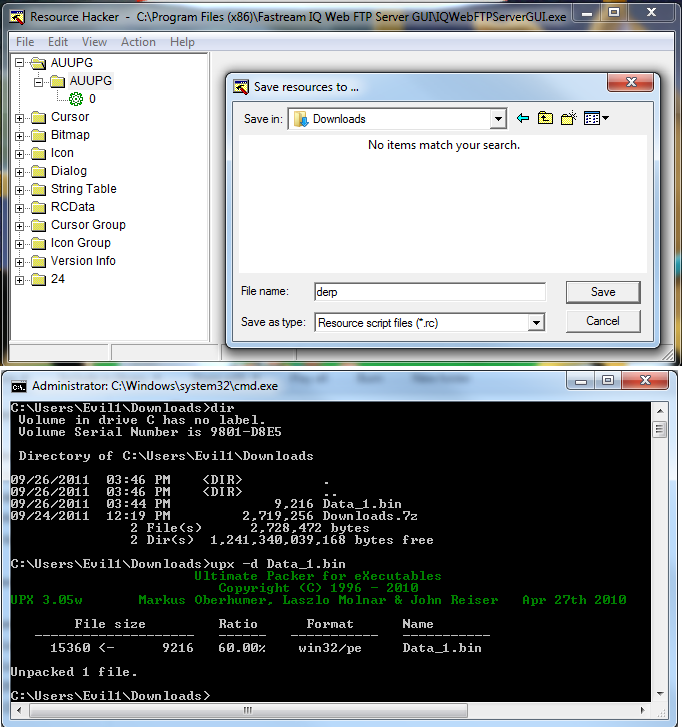
See the string? “This program cannot b e run under win32”. Yeah, there’s a program stuffed in the resources table. And not just any program if you’ll notice the dead give away a few dozen null bytes in. UPX 1 UPX 2. That’s right, a PACKED executable in the resources table. Weird. So how do we get it out? Save the resource as a .bin file and run against UPX of course!
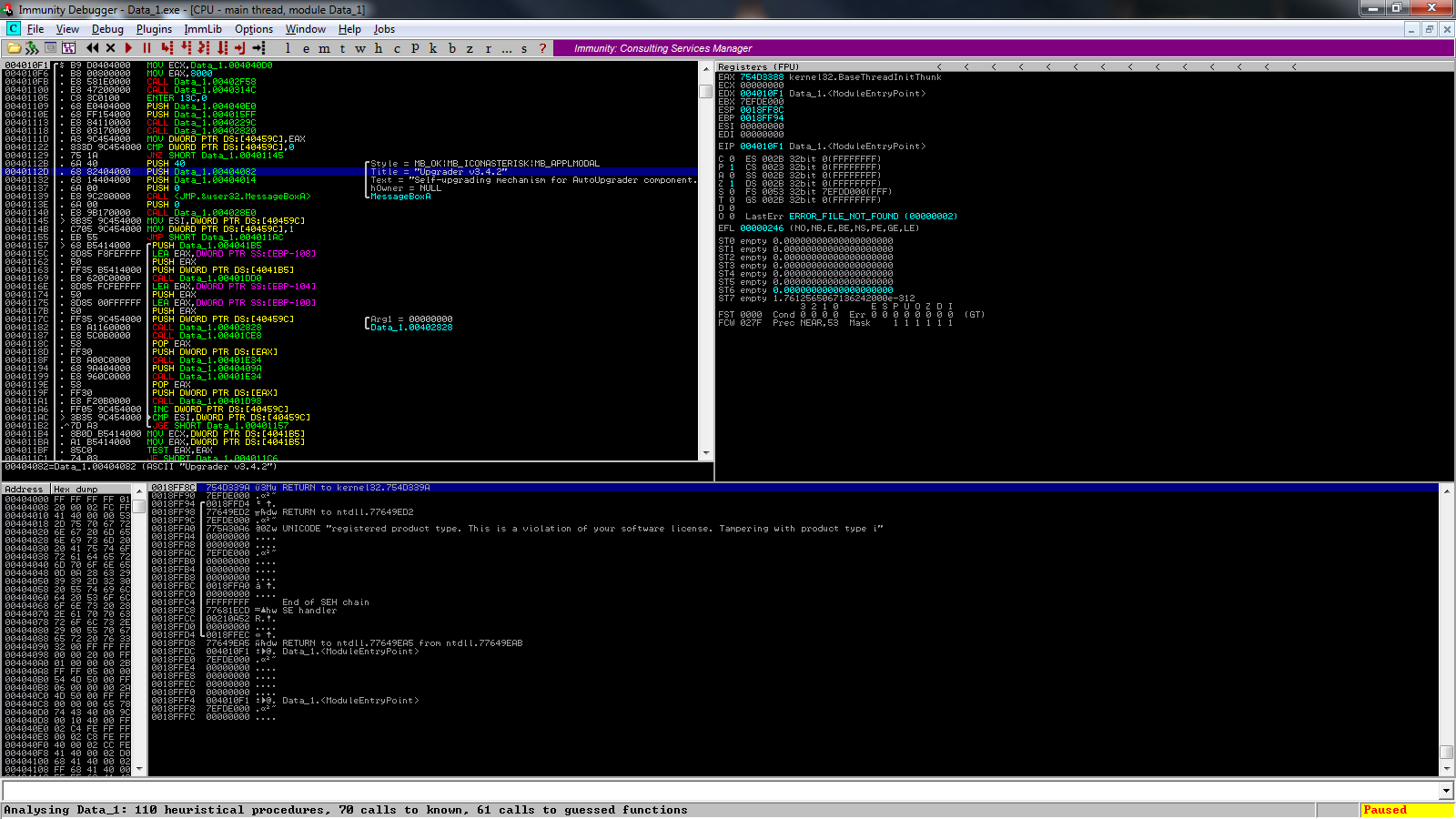
That’s an odd place to put a program. A clever place to store your copy protection string. I stumbled upon this program on accident. I’m sure you’re all wondering what the hell it is. Its the program’s self updater / authenticity checker. See?
The point I wanted to convey in this posts is that developers are smart. Smarter than we give credit to some times. Imagine if this program were packed with some packer not known to the rest of the world. Or worse, there was some checksum in the program that got mad if you tried to remove the resource. By the way, since it IS a a resource string, you CAN remove the program using any conventional resource editor.
Tools used – upx, reshacker, resedit, immunity.