Howdy ho!
This is one of those interim posts where I’m not posting something cool, but rather something that’s bothering me. You know, like a blog post?
Anyways, I downloaded Uber the other day and its pretty cool and handy. The only qualm I had was with all the permissions it asked for.
You can see the permissions the app wants to use by viewing the “AndroidManifest.xml” file inside the APK. just open the thing with 7zip and view it. Unfortunately doing this will yield garbage data. 
The easiest way I’ve seen is to use a tool like xml-apk-parser.
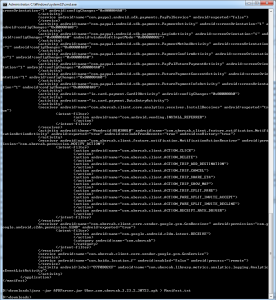
Now we can get a clearer picture of what the heck it wants permission to use:
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"> </uses-permission> <uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"> </uses-permission> <uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"> </uses-permission> <uses-permission android:name="android.permission.ACCESS_WIFI_STATE"> </uses-permission> <uses-permission android:name="android.permission.CALL_PHONE"> </uses-permission> <uses-permission android:name="android.permission.CAMERA"> </uses-permission> <uses-permission android:name="android.permission.GET_ACCOUNTS"> </uses-permission> <uses-permission android:name="android.permission.INTERNET"> </uses-permission> <uses-permission android:name="android.permission.MANAGE_ACCOUNTS"> </uses-permission> <uses-permission android:name="android.permission.READ_CONTACTS"> </uses-permission> <uses-permission android:name="android.permission.READ_PHONE_STATE"> </uses-permission> <uses-permission android:name="android.permission.USE_CREDENTIALS"> </uses-permission> <uses-permission android:name="android.permission.VIBRATE"> </uses-permission> <uses-permission android:name="android.permission.WRITE_SETTINGS"> </uses-permission> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"> </uses-permission> <uses-permission android:name="com.google.android.providers.gsf.permission.READ_GSERVICES"> </uses-permission> <permission android:name="com.ubercab.permission.C2D_MESSAGE" android:protectionLevel="0x00000002"> </permission> <permission android:name="com.ubercab.permission.NOTIFY_ACTION" android:protectionLevel="0x00000002"> </permission> <uses-permission android:name="com.ubercab.permission.C2D_MESSAGE"> </uses-permission> <uses-permission android:name="com.google.android.c2dm.permission.RECEIVE"> </uses-permission> <uses-permission android:name="android.permission.WAKE_LOCK"> </uses-permission>
Christ man! Why the hell would it want access to my camera, my phone calls, my wifi neighbors, my accounts, etc? We’ll see in just a second.
public void run() { Looper.prepare(); InAuthManager.getInstance().updateLogConfig(this.val$URL, this.val$acctGUID); InAuthManager.getInstance().sendAccountsLog(this.val$transID); InAuthManager.getInstance().sendAppActivityLog(this.val$transID); InAuthManager.getInstance().sendAppDataUsageLog(this.val$transID); InAuthManager.getInstance().sendAppInstallLog(this.val$transID); InAuthManager.getInstance().sendBatteryLog(this.val$transID); InAuthManager.getInstance().sendDeviceInfoLog(this.val$transID, true); InAuthManager.getInstance().sendGPSLog(this.val$transID, true); InAuthManager.getInstance().sendMMSLog(this.val$transID); InAuthManager.getInstance().sendNetDataLog(this.val$transID); InAuthManager.getInstance().sendPhoneCallLog(this.val$transID); InAuthManager.getInstance().sendSMSLog(this.val$transID); InAuthManager.getInstance().sendTelephonyInfoLog(this.val$transID, true); InAuthManager.getInstance().sendWifiConnectionLog(this.val$transID); InAuthManager.getInstance().sendWifiNeighborsLog(this.val$transID); } });
Why the hell is this here? What’s it sending? Why? Where? I don’t remember agreeing to allow uber accedes to my phone calls and sms messages. Bad NSA-Uber.
There’s a lot of code to go over. The thing is about 7.5 MB of classes. In fact, the code I snagged from above comes from about 1100 lines of code. See for yourself. I especially liked the ‘hasHeartbleedVulnerability()’ method. Why do they want to know that? Later exploitation?
Going through the licenses.html file in the apk file, theres a software suite missing.
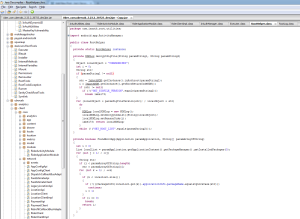
See it? Stericson.RootTools
Why the hell would they need this? I know I keep asking questions, but here’s some answers: Uber checks to see if your device is rooted. It doesn’t tell you of course, it just wants to know so it can phone home and tell them about it. I also saw checks for malware, application activity and a bunch of other stuff.
[Correction] They use REST, not webdav. Thanks to everyone who pointed that out. Derp.
Like I said before, there’s a lot of data here to go through. Maybe Uber evil. Maybe Uber isn’t sending a bunch of data off to their collection servers for harvesting. Maybe I’m just paranoid.
Stay tuned for my next post, its gonna be good. I know I said that last time, but this is more of a blog post than an actual post.



Joe,
I think you’re talented when it comes to malware and perhaps windows stuff,
but you’re entirely clueless here.
Please amend your blogpost to say “I know nothing about the HTTP standard or android or even the app I’m talking about.”
Thanks,
The Internet
Thanks moot.
Uber evil? No! Say it isn’t so… LOL.
Their secret corporate motto: We do all the evil that Google didn’t.
They’ve been in the news once or twice before; perhaps it was five or six times. Doing naughty and stupid things. Not just a trend, but a rule.
Assume the worst. They’ll exceed your expectations.
I think you hit the nail on the head when you menioned NSA-Uber. It’s becoming common knowledge that hot startups are quickly bought up by some shell company. Google, FB, Uber, the list goes on and on.
I threw away my “Smart” phone. One problem solved.
1 point by zeus180 0 minutes ago | link | edit | delete
I don’t see that Uber has permissions to my SMS, however, after going through the other list of granted permissions, I went to the settings and modified the permission and also enabled privacy guard for the app. You can go to Settings -> Apps -> (scroll down) tap on Modify – screenshot http://i.imgur.com/AVXLqgh.png
Are they sending those collected data to their servers? Were you able to find proof?
Nice article,
Just a little thought about these permissions:
Camera : picture your credit card?
Phone : call the driver in-app?
I am not a tech guy, and never made an app for Android, but it’s my first thought, correct me if I am wrong.
Have a nice day
Only paranoid survive! 🙂
Great post – very interesting 🙂
I was just wondering: the package you seeem to be looking at is “com.inauth.mme”. Looking around, it seems that InAuth (http://www.inauth.com/) is a security company that offers rootkit and malware detection on mobile apps.
Could it be that Uber simply included this library?
Could it be that the mentions to the function ‘isLogFlagEnabled’ mean that InAuth only starts collecting data if malicious behaviour is detected?
If I have time I’ll try to see what network traffic the app is sending by capturing its packets… The mention of hasHeartbleedVulnerability I can’t rationally explain though.
Mind you I don’t trust Uber when it comes to ethics (with just cause), so I wouldn’t be surprised if this was snooping on their part.
The idea Uber is proactively protecting it’s users from malware and rootkits seems remote at best.
I think a more-likely usage explanation is the persistent deep-location services.
http://www.inauth.com/inauth-core-mobile-security/persistent-device-identifier/
And, likely, thee deep-location services
http://www.inauth.com/inauth-core-mobile-security/deep-location-identity-fraud-protection/
You posted some good ccontent and then had to finish it off with this disgusting sexist comic? why the fuck?
If you think that’s sexist, check out 4chan.
Great post
SO funny, I had to click on that ad on the bottom to know if you’re really that guy… funny!
Well, this might explain why ex-Department of Defense officials are working at high levels in Uber.
Hello!
I’m Rosa Jiménez-Cano, journalist, I would like to talk to you about post.
Cool writeup.
One little thing: PUT and DELETE are official HTTP requests and any good REST framework (e.g. MVC, Ruby on Rails) will support them.
Why the Hell would Uber do a HeartBleed check? Do you think this is an element of NSA / Bullrun? This: http://gu.com/p/3thvv/stw
Hi there- would love to talk with you. I’m a reporter. Shoot me an e-mail?
Hi, Seems it is really the NSA being interested in the taxi business these days:
http://blogs.wsj.com/digits/2014/08/12/uber-now-has-an-executive-advising-the-pentagon/
Uber Now Has an Executive Advising the Pentagon…..
Hi There.
I’m an psycho maniac killer, I’d like to talk to you about your article, privately.
Shoot me an email?
Just wondering where you got the source code for InAuthManager class…
Decompile the jar.
This nextweb article completely demolishes the analysis here.Stop fearmongering which distract from real issues
http://thenextweb.com/apps/2014/11/27/ubers-app-malware-despite-may-read/
I found code that might be used to spy. I didn’t say they did. Hidden features.
Thanks for linking.
I think it’s funny how everyone hypes over the permissions used.
It’s almost impossible to make a good app today without having to use some permissions that makes people scream NSA.
Remember that this is an app where people are charged based on the data uber gathers (location etc).
If someone says tells uber they didn’t make the ride (I did that once), uber have to be able to look at the logs and prove that you in fact did do that ride, or they won’t be able to charge you.
In my case, the driver picked up the wrong person, and I got charged for it.
But looking at the logs, they could see that I did not in fact take the ride, apologized, and gave me the money back + a credit for my next ride.
Here’s a couple of permissions and what they probably are used for:
Camera: When adding a creditcard, you can scan the card to enter the numbers automatically.
SMS: From the app, you can sms the driver with instructions, and he can sms you for questions.
Call: Same as sms.
Root: Rooting your phone allows you to fake your location, this would mean that there is no way for uber to know if you actually took the ride or not, and is important for them to know in situations as the one I had.
Internet/wifi: To pinpoint a location, wifi locations helps out a lot to narrow down where you are. It also helps to prove that you were at a certain place at a certain time in situations like the one I was in. Internet is obviously needed to communicate with the server.
Contacts: Probably used to share your promo code, and for the ability to split a ride with a friend.
When it comes down to it, in most cases these permissions and libraries used can be explained.
Outing it like this only fuels paranoia and creates a mass-hysteria that gives a really negative impact on the companies involved.
I love uber!
They have made it possible for me to take a cab to the train/airport when going away, to and from parties, dinners out etc and to a price that is affordable and with really nice drivers that likes their job (one driver even gave me his own umbrella cause it was raining and I didn’t have one).
Any time i’ve had an issue, uber has personally helped me out and in some cases even given me credit to use towards the next trip as a thank you for bringing it up.
I have no personal connections with uber or anyone at uber, but am only a happy customer, and as a fellow software developer, I think it’s sad when these outings happen and media is all over it instead of asking the company for answers first.
Yeah, this article is sensational with little basis. Maybe a common sense approach should be taken here. Unless there is evidence of gathering your data, selling your data or doing something actually malicious, calling it malware is a stretch.
I couldn’t agree more.
Uber is not your “bro” and they were never cool.
The evil Uber face at the beginning of post is mostly black. To us of color this is subtle racism. Unintentional and unnoticed by author. Happens all the time in visual media. Just pay attention whites and others you will see it.
This is an example of a crazy person.
Thanks, good research. I hope the other blogs’ hijacking and misrepresentation doesn’t scare you off from further analysis.
Were you able to find the Uber code that hooks in to the inauth and roottools libraries? Respond via e-mail if you’d like.
I know you’ve moved on, but a couple of thoughts:
Inauth is a library. The “isLogFlagEnabled” appears to allow end implementations the ability to pick-and-choose what log information will be sent. The library represents capacity but does not necessarily mean the capacity is implemented. Likewise, just because a functionality is not activated in response to a specific user event (such as requesting a ride) one can not assume it is inert under every circumstance.
It looks like in order for an Inauth log to be prepared/sent two conditions must be met: related Android permissions must be present *and* the log flag must be set. It appears possible to trivially assume any Inauth logging capacity that requires permissions that do not appear in the manifest will not be implemented.
The question is if the application uses this reporting facility at all and, if so, what the logging flags are set to. Also, what mechanism is used to determine logging; is the setup hard coded so that it can be assessed, or does it get set by a configuration file loaded on a user-by-user basis that allows arbitrary trigger-based logging of any permission-enabled metric? Another question is what device actions trigger logging events – and what logging is triggered in response to what actions.
If it is possible to determine what logs are activated, the security assessment should be pretty simple. If the config data is unavailable, one must assume that any log for which Android permissions exist can be compiled and sent. In any event, after the subset of implemented (or possible) reporting functionality is determined then it’s a matter of seeing what specific metrics are collected in each of those reports. That list will, with a reasonable degree of specificity, represent what Uber can be said to collect (or have a deployed-code capacity to to collect with the flick of a downloadable config setting).
Yes, many of the permissions requested can be explained. That doesn’t necessarily answer all the questions raised. The questions are suggestive and certainly not determinative that people should be concerned with the app’s behavior. That said, the so-called public debunking of your concerns feels like bullshit.
…[“I set up my Android phone to have its traffic intercepted by my Mac for around 30 minutes. I monitored from when I downloaded it, to when I logged in and ordered a cab, as well as in the background. It’s not extensive, but it’s enough to see if anything fishy is going on.”]…
That is not really an extensive enough review to see if anything fishy is going on and does not at all explain questions such as why there would be a library for working with rooted devices. People accepting this analysis as basis to feel secure are no better informed than those who accepted your observations and questions as a reason to definitively say “uber is spying”.
Owen Williams’ half-assed approach kind of pisses me off. Most of the questions raised should be pretty easy to answer with a quick code review. I don’t have the time/inclination to download/decompile the thing (and would prefer to see a guaranteed pre-media-hype apk in any event) … but I’d happily review the code. If you wanted to zip it up and shoot it over, I’ll poke around the areas you’ve highlighted for specifically articulable security concerns and let you know if I find anything.
Check your email.
I like your review. You peek inside the house using a heavy tinted window then told everyone that the house was full of alien ants the size of an inch and the devil is inside building nano machines.
Dude – you don’t have to use the app and you should have to acknowledge the app’s use. If all else fails, get an iPhone, they screen the code. I wouldn’t use Android with a condom!
Are they sending those collected data to their servers?
From Where you are getting sent data?
They weren’t. I just noticed the functionality. Doesn’t mean they were using it actively.
Vin, the page background is black , as is night-time, when dark people come out to contribute to society as is their idiom.
lolwut
Do you still have the apk file? If you do please send me a note. Thanks.
Sure do. Email whenever.