Hello loyal readers!
Sorry for the delay in posts, I’ve just been busy with life. Anywho, I got some code to share. A lil script I put together for scanning office documents for the Sandworm exploit. aka Microsoft Security Bulletin MS14-060.
For those of you who don’t know / live under a rock, its a recent vulnerability in PowerPoint that can be used to run code and it DOESN’T require shellcode making it highly favorable / reliable for malware people.
The way it works is a specially crafted PPT document allows a malicious user to load an INF file. INF files are quite powerful in what they allow you to do – load files, mess with the registry, etc. Here’s what one such INF file looks like:
; 61883.INF [Version] Signature = "$CHICAGO$" class=61883 ClasGuid=%Msft% DriverVer=0/21/2006,61.7600.16385 [DestinationDirs] DefaultDestDir = 1 [DefaultInstall] RenFiles = RxRename AddReg = RxStart [RxRename] penguin.exe, cedt370r(3).exe [RxStart] HKLM,Software\Microsoft\Windows\CurrentVersion\RunOnce,Install,,%1%\penguin.exe
In the above sample, the INF file would add a certain exe to auto-run the next time the computer is rebooted.
So how do we detect such an attack in a PPT document? Easily. Search for INF file artifacts!
import struct import sys import zlib ole_object_header = "\x10\x00\x11\x10" gzip_header = '\x1f\x8b\x08' + '\x00' * 7 with open(sys.argv[1], "rb") as f: data = f.read() n_objs = data.count(ole_object_header) print "%d objs found" % n_objs pos = -1 for i in range(n_objs): d = zlib.decompressobj(zlib.MAX_WBITS | 32) pos = pos+1 + data[pos+1:].find(ole_object_header) compressed_len = struct.unpack("I", data[pos+4:pos+8])[0] try: obj = d.decompress(gzip_header + data[pos+12:pos+12+compressed_len-4]) except zlib.error: obj = '(zlib error)' # find INF file artifacts within ole_objects look1 = "\[Version\]" look2 = "DriverVer" if look1 and look2 in obj: print "found inf file in stream # ", i else: print "Found no inf in stream # ", i
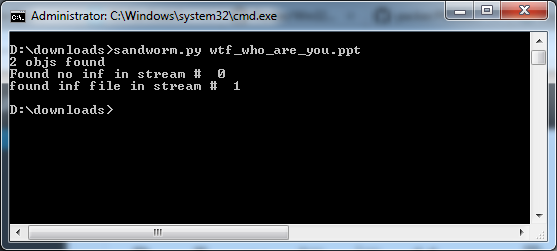
Code in action:
All my code does is search a binary stream for an OLE header, then searches for the gzip header, then extracts the data, then looks for the artifacts. Simplicity is golden.
Stay safe out there!