Howdy fellow h4x0rs & Cr4x0rs alike!
Today I ran into some vmware aware malware and it threw me off until I ran procmon and apispy. I had to patch the program to skip the checks, but I don’t want to get into that. Instead, let’s cover what this malware was checking.
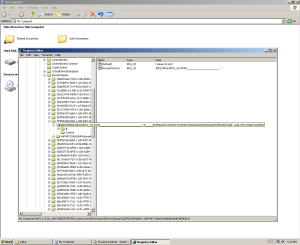
First off, it was checking for VirtualBox specific registry key and hardware settings. This is easy to check for assuming you know some code:
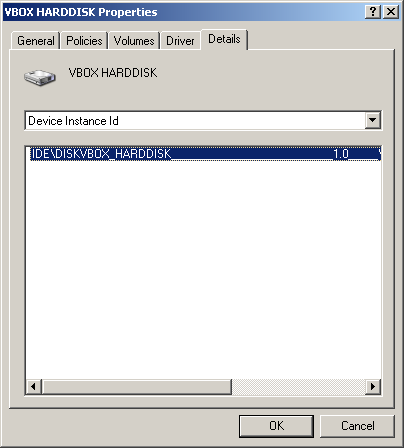
If you check the cdrom and hard drive for their device ID’s or merely look for the word ‘vbox’ inside the HKLM\systen\currentcontrolset\control\deviceclasses\ hive, chances are good you’re in a virtual machine like virtualbox.
Too complicated? WMI and .NET to the rescue!
using System; using System.Management; class Program { static void Main(string[] args) { ManagementObjectSearcher moSearch = new ManagementObjectSearcher("Select * from Win32_DiskDrive"); // wanna search cd rom drives? // ManagementObjectSearcher moSearch = new ManagementObjectSearcher("Select * from Win32_CDROMDrive"); foreach (var mo in moSearch.Get()) { Console.WriteLine("Device Instance Id: " + mo["PNPDeviceID"].ToString()); // or mo["DeviceID"] } Console.Read(); } }
A simple WMI query can check against installed devices. A simple string.contains() comparison for ‘vbox’ will suffice.
There’s one other method worth pointing out. The shared folders method. VirtualBox creates a shared folder that’s navigable like a share.
if(Directory.Exists(@"\\VBOXSVR\")) { Console.WriteLine("GTFO!"); }
Just check to see if you can access the ‘\\vboxsvr’ share. Normally this folder is read write execute (777) and free reign for other programs by default.
The malware I ran into also took it a step further by doing DNS queries to both google.com as well as sun.java.com before making its true call out. Clever, but ultimately pointless and easy to catch when you can just switch the host names out in the c:\windows\system32\drivers\etc\hosts file. If it were me, I would take further precautions such as doing an md5 checksum against a favicon or something. Oh wait, I already suggested that.
Oh well.
Happy hacking!