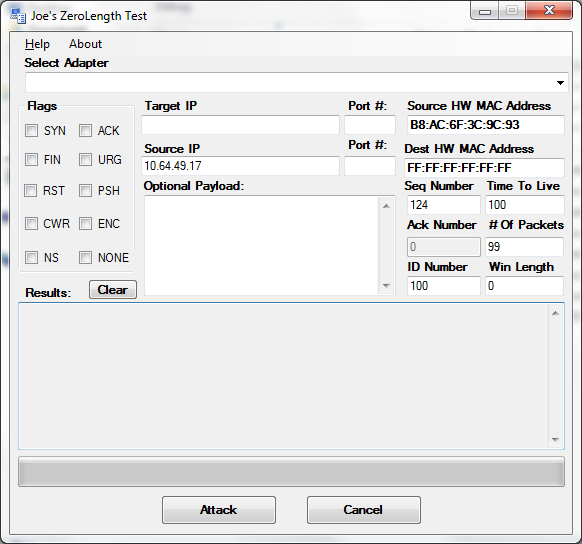
Hello again people!
I’ve been busy lately with my awesome job giving me free time to code things up. I’ve constructed a raw TCP packet builder in C# for the hell of it. I coded this up using winpcap to test a topic I saw at Defcon this year. It was said a vulnerability exists in the TCP stack for Windows and Linux having to do with the ‘window length’ bit in a TCP packet. Specifically if you flood a target with TCP packets full of data, but set the ‘windows length’ bit to 0, you are telling the host that your reserves are full and need the destination’s stack to hold the data for a while.
I could have done with with scapy or some other interpreted language, but I wanted to make a tool with a dummed down interface any idiot could use. C# to the rescue for that.
It works for testing the vulnerability because it sets the length to 0 no matter what TCP flags you set or what payload you give it. It’s also great for syn flooding your neighbors.
This is an alpha version. The tool has bugs, but it works. Be sure to install winpcap (and START the service) for this to work.
Source /Binary is here:
PacketMaker
The password is ‘gironsec’ without quotes.