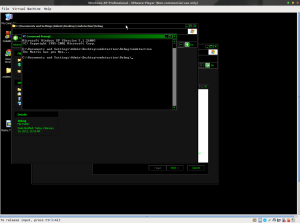
Ladies and gentleman – I give you yet another case of VMware detection. Unfortunately, this only works for VMware. A friend of mine, one Aaron Yool told of me a way to detect VMware via the use of privileged instructions. Specifically the “IN” instruction. This instruction is used for reading values from I/O ports. What the heck is that? According to the IA32 manual, I/O ports are created in system hardware by circuity that decodes the control, data, and address pins on the processor. These I/O ports are then configured to communicate with peripheral devices. An I/O port can be an input port, an output port, or a bidirectional port. Some I/O ports are used for transmitting data, such as to and from the transmit and receive registers, respectively, of a serial interface device. Other I/O ports are used to control peripheral devices, such as the control registers of a disk controller.
Dry material huh? That’s the Intel manual for you.
Normally you can’t execute this instruction on Windows in user mode – its a SYSTEM instruction like HLT which are reserved for ring 0. On VMware however, you can call it from ring 3.
What can be done if a user mode program and run system level instructions? The sky is the limit, but think rootkit without admin. Pretty wicked stuff. Is this the case here? No, not yet anyways. For now though, we have here a simple way of checking to see if we’re inside VMWare, POC included. We’re using SEH (Structured Exception Handling) here in case Windows complains about the instruction being privileged.
Who here likes code? I do!
// ------------------------------------------------------------------------------ // THE BEER-WARE LICENSE (Revision 43): // <[email protected]> wrote this file. As long as you retain this notice you // can do whatever you want with this stuff. If we meet some day, and you think // this stuff is worth it, you can buy me a beer in return // ------------------------------------------------------------------------------ #include <iostream> #include <windows.h> unsigned vmware(void) { __asm{ mov eax, 0x564d5868 mov cl, 0xa mov dx, 0x5658 in eax, dx cmp ebx, 0 jne matrix xor eax, eax ret matrix: mov eax, 1}; } int seh_filter(unsigned code, struct _EXCEPTION_POINTERS* ep) { return EXCEPTION_EXECUTE_HANDLER; } int _tmain(int a, _TCHAR* argv[]) { __try { if(vmware()) goto matrix; } __except(seh_filter(GetExceptionCode(), GetExceptionInformation())) { goto stage2; } stage2: std::cout << "Isn't real life boring?"<<std::endl; exit(0); matrix: std::cout << "The Matrix haz you Neo..."<<std::endl; exit(1); }